Cybersecurity awareness is crucial for IT projects and even projects without a specific IT focus. To create awareness about cybersecurity in your workplace, we need to make essential cybersecurity habits part of your work culture and identify cybersecurity risks in your risk register. In this March Dinner meeting, Kristine Hayes-Munson addressed how to make cybersecurity part of your communications management plan. She expressed being aware of the software’s terminology and that PMs should be aware of how it related to cybersecurity.
In the Dinner meeting presentation, Kristine Hayes Munson discussed the impacts on a project. Kristine covered topics like how to review information security and privacy regulatory environment. She shared lessons learned from security breaches, enforcement actions, and fines. Kristine also gave key steps to identify information security and privacy impacts in your project.
Speaker Bio

We invited Kristine Hayes Munson to our March 2023 dinner meeting. Kristine A. Hayes Munson, MBA, PMP, CIA, CISM, is an IT leader with a proven track record of completing IT projects in the finance industry. She specializes in implementing high-profile, cross-discipline projects resulting in deliverables aligned with the organization’s strategic objectives. She oversees a risk and compliance program balancing internal controls, regulatory requirements, information security best practices, and entrepreneurialism.
Ms. Hayes-Munson’s interactive presentations and courses integrate project management theory with hands-on, experiential learning. She is a member of the University of California Irvine Extension’s project management certificate program’s faculty. She has presented at multiple professional association events, including PMI North America Global Congress (Vancouver and San Diego), Richmond Events CIO Forums (San Diego, San Francisco, and New York), Southland Technology Conference (Long Beach), and PMI-Orange County Advanced Topic Seminars (Irvine).
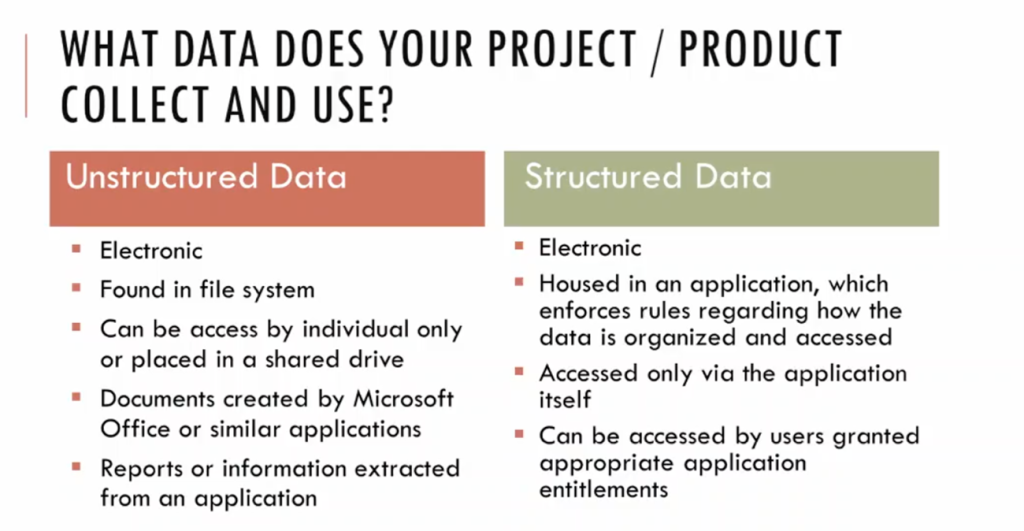
Speaker Kristine shared that there are two types of data, Structured and Unstructured. Structured data is predefined and formatted to a set structure before being placed in data storage, which is housed in applications and accessed only through the application. Users can access the Structured data granted appropriate application entitlements. The best example of Structured Data is the relational database: the data has been formatted into precisely defined fields, such as credit card numbers or addresses. Unstructured Data is everything else that is more difficult to categorize or search, like photos, videos, podcasts, social media posts, and emails. Most of the data in the world is Unstructured Data. Unstructured data can be accessed by individuals only or placed into a shared drive.
Data Security is essential in the workplace. By adopting data security techniques and technologies, such as physical hardware (ie. storage devices) security, logical security for software applications, administration and access controls, organizational policy standards, and other data security practices, organizations can help organizations secure their cyber security in the workplace.

PMs play an essential role in cultivating a cybersecurity workplace culture. The most common cyberattacks stem from phishing, where hackers pose as trusted entities to steal sensitive data and credentials. So, instead of trying to break into password-protected networks, cybercriminals turn their attention to employees, unwittingly providing the necessary information. Phishing attacks often contain links or attachments that allow hackers to access the target’s network. PMs can best protect their project and avoid data theft by educating their employees on proper cybersecurity protocols. For example, tell employees never to open links or attachments unless they know they are safe, or create a unique email signature that lets employees know the email is legitimate. The PMs must also understand the importance of least-privileged access and patch management.

1. Least Privileged Access
The best cybersecurity practice in an organization that project managers should be aware of is the principle of least privilege (PoLP). This is where you protect the project’s data by protecting privileged access to high-value data and assets. In the principle of least privilege (PoLP), users are given the minimum levels of access – or permissions – needed to perform their job functions.

2. Create Awareness Among Employees About Social Engineering
Social Engineering manipulates humans into sharing facts they shouldn`t share, downloading software programs they shouldn`t download, touring websites they shouldn`t visit, sending cash to criminals, or making different errors that compromise their non-public or organizational property or security. In many instances, cybercriminals use social engineering techniques to acquire the sort of non-public data—login credentials, credit score card numbers, financial institution account numbers, and Social Security numbers that they can use for identity theft. All these allow them to make purchases using peoples` cash or credit scores, observe for loans in a different person’s name, observe for different peoples` unemployment benefits, and more. A social engineering assault also can be the primary level of a larger-scale cyberattack. For example, a cybercriminal may trick a sufferer into sharing a username and password—after which they use the credentials to plant ransomware at the sufferer`s employer`s network. Social engineering is appealing to cyber criminals as it permits them to get admission to virtual networks, gadgets, and bills while not having to do the hard technical paintings of hacking firewalls, defeating antivirus software programs, and obtaining different cybersecurity controls.
Project managers must educate their teammates about conducting and continuously refreshing security awareness. PM can encourage using multi-factor authentication when giving access to the software. The speaker mentioned that as the workplace changes and more employees work outside the office, companies require more advanced multi-factor authentication solutions to manage more complex access requests. Multi-Factor Verification could be anything from Biometric Access and security questions to an OTP code.
3. Encourage practicing patch management at work.
Speakers discussed how important it is for project managers to encourage Patch Management in their projects. Patch Management is updating software with new code. In most cases, the purpose is not only to fix vulnerabilities that can be exploited by hackers but also to fix other problems in existing programs or to add new features. Stay up to date with the privacy framework, standards, and regulations related to cyber security.
The speaker addressed that it is not possible for PMs to investigate all the cybersecurity protocols and make changes by themselves; they need to use their networking skills and connect with the cybersecurity team in the organization and HR department to implement the necessary cybersecurity protocols.
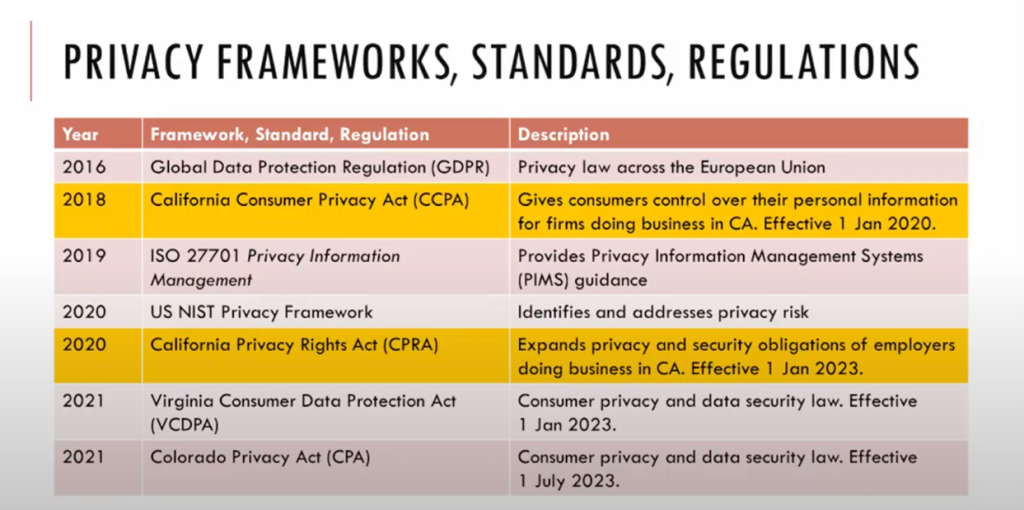
During the presentation, the speaker shared some standards and regulations.
The California Consumer Privacy Act of 2018 (CCPA) gives consumers more control over the personal information that businesses collect about them, and the CCPA regulations provide guidance on how to implement the law. The California Privacy Rights Act of 2020 (CPRA), also known as Proposition 24, intends to provide California residents with the right to know who is collecting their and their children’s personal information, how it is being used, and to whom it is disclosed. It is helpful to control the use of their personal information, including limiting the use of their sensitive personal information. It should be noted that the consumer can have access to their personal information and the ability to correct, delete, and transfer their personal information.
The speaker concluded the presentation with a note for all the participants to always the value of the project data, whose data it is (customers and/or clients), and the potential effects if it were breached. Project managers (PMs) should know how much data – and of what kind – will be affected in the event of a breach. As PMs, we cannot have all the knowledge required for cyber security, but we can connect with the subject matter expertise in cyber security and encourage the team to practice secured data security protocols.